

Yeah, this is FSKAX over 3 years. I have a lot of my portfolio in it and it does well. It’s up 24% over that period.
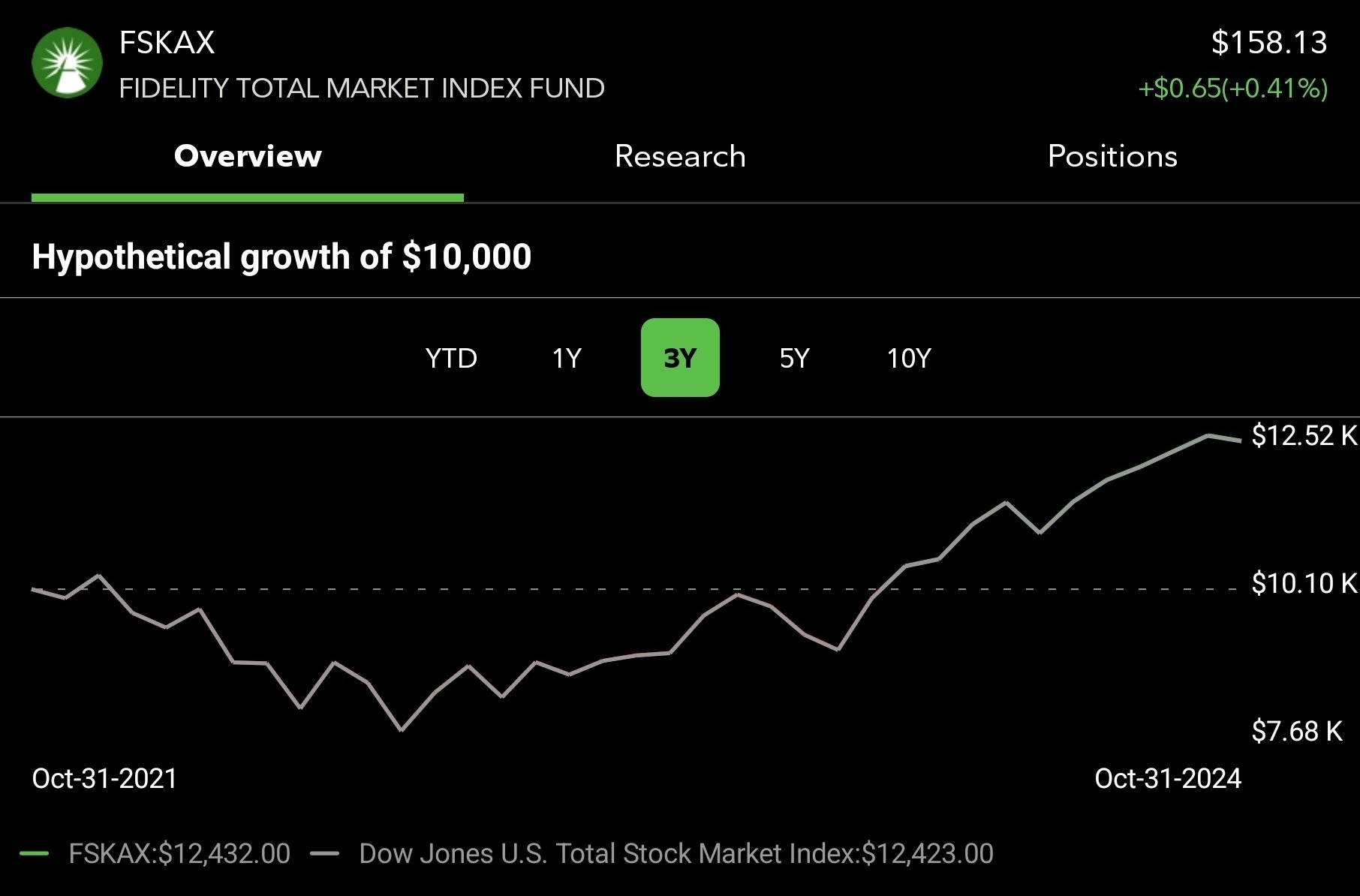


Yeah, this is FSKAX over 3 years. I have a lot of my portfolio in it and it does well. It’s up 24% over that period.



Then you apply the scientific method and/or research in search of truth.


Yes! Basic Training in 3-2-1 Contact.



I’ve been using Droid48 forever. It’s perfect.


Use a Chromium browser to inspect the cert.
If anyone knows how to get Firefox to show a bad cert before loading the page, I’d love to know.


Assuming you’re the one adding HSTS, you’ll have to inspect the cert and/or view the content that is getting returned. On desktop Chromium you can type “thisisunsafe” to load a page even with HSTS. Not sure how to do it on mobile FF.
Would seem weird for it to be intercepting your domain’s traffic but not the rest of the internet.
Edit: just noticed you’re not even loading an SSL page. Are you using https in the URL?


I’m not sure about color support without HTML or add-ons, but Obsidian is a good markdown editor with a lot of functionality and extensibility.
It’s not open source but it runs on everything.
If you’re sure you’ve got a DNS entry for the Pihole FQDN pointing at Traefik, open the dev panel in your browser (F12), switch it to the Network tab, and visit the pihole URL.
See if you get anything back and especially take note of the HTTP status codes.
Can you see the router and service in the Traefik dashboard and do they show any errors there?
I think you’re close.
You need to change service: pihole-rtr to service: pihole-svc.
Do I have to redefine all of the same information I did in my Traefik yml but in this separate config.yml?
No, you just need to reference it like you have. Define once, reference many.
No worries for the question. It’s not terribly intuitive.
The configs live on the Traefik server. In my static traefik.yml config I have the following providers section, which adds the file provider in addition to the docker provider which you likely already have:
providers:
docker:
endpoint: "unix:///var/run/docker.sock"
exposedByDefault: false
file:
directory: /config
watch: true
And in the /config folder mapped into the Traefik container I have several files for services external to docker. You can combine them or keep them separate since the watch: true setting tells it to read in all files (and it’s near instant when you create them, no need to restart Traefik).
Here is my homeassistant.yml in that folder (I have a separate VM running HASS outside of Docker/Traefik):
http:
routers:
homeassistant-rtr:
entryPoints:
- https
service: homeassistant-svc
rule: "Host(`home.example.com`)"
tls:
certResolver: examplecom-dns
services:
homeassistant-svc:
loadBalancer:
servers:
- url: "http://hass1.internal.local:8123"
Hope this helps!
I use the Traefik file provider for this.
https://doc.traefik.io/traefik/providers/file/
It picks up all my .yml configs in the watched folder which define the routers and services external to Docker.
I know plenty account SNI already, but thanks. You might want to study more yourself, since we’re being condescending.
So now your ISP sees all of your queries instead of CF. (Assuming the cloudflared option is using DoH)
I’ll trust Cloudflare over Comcast/AT&T/etc. any day of the week.


I found it amusing that these posts were adjacent.



I believe you. I’m just saying their non-firewalls (i.e., switches and APs) don’t have that limitation.


My firewall is a Fortigate 60F.


I would never use their firewalls/gateways, but their switches are pretty good for the price and their APs are decent (although tbh after 3 generations my next AP will likely be an enterprise Aruba).
That said, I still use Unifi in docker, everything is up to date, and nothing is requiring a sign-in to the cloud. Am I missing something? If it’s just the firewalls, then I’m not surprised since I’ve never been remotely tempted to use them, but it sure isn’t all of their devices.
Holy shit, I remember being excited for 2.4 because of iptables. That was over twenty years ago.